
VMware Cloud Director (VCD) was designed from the ground up with multi-tenancy in mind. It is a product that enables multiple customers or tenants to use the VMware Software-Defined Data Center (SDDC) infrastructure while maintaining strict isolation, security, and resource allocation.
VMware NSX has provided a multi-tenant data-plane model since the beginning of the product. Still, it started to support management plane multi-tenancy with the introduction of NSX Projects in version 4.0.1.1 (API) and in 4.1 in the UI.
Naturally, to improve the integration with NSX and unlock a number of networking features, VCD development evolved so that the latest 10.5.1 release now adopts the NSX Mutli-Tenancy model. Read more about NSX Multi-Tenancy journey.
Concepts
In the VCD platform, tenancy is implemented through the use of the Organizations. Each tenant is assigned a dedicated organization, providing a logically segregated virtual infrastructure and resources for their workloads. The Organization construct allows for fine-grained control over the tenant’s access to resources and enables the tenant to manage their own Users, Virtual Data Centers (VDCs), Catalogs, Policies, and more.
To explicitly define the tenant paradigm, VMware NSX implemented a solution called Projects. These Projects delegate NSX users to different spaces with their own objects, configurations, and monitoring (based on alarms and logs).
VCD 10.5.1 provides management capabilities associated with NSX Tenancy, which are exclusively in the Provider’s scope. The NSX Tenancy feature is available per Organization basis, and when enabled, a VCD Organization maps directly to an NSX Project.

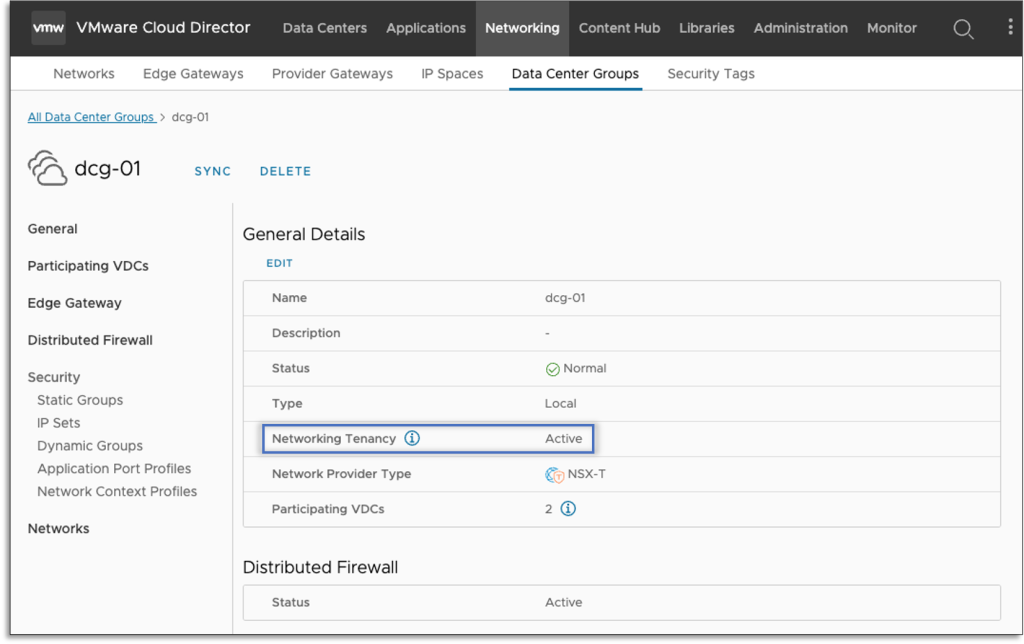
After the NSX Tenancy is enabled at the Organizational level, Providers can create Organization Virtual Data Centers (VDCs) with Networking Tenancy enabled via the Org. VDC creation wizard.
Any existing VDCs and Data Center (DC) Groups owned by that Organization are considered brownfield and have the Networking Tenancy “Inactive”.
It’s important to note that VCD cannot recognize and import existing NSX Projects. In order to use Networking Tenancy within the context of VCD, providers must first define the Organization within VCD and then to enable the Networking Tenancy.
VCD Networking Tenancy Details
When a Provider enables the NSX Tenancy (Networking Tenancy) for a specific Organization, he can also define a Log Name. This is the Organization’s unique identifier in the backing NSX Manager logs.

Activating the Networking Tenancy for the Organization does not trigger immediate NSX Project creation. Instead, the NSX Project gets created when the first Networking Tenancy enabled VDC is created. The NSX Project name corresponds to the Organization name, though.

By default, the Networking Tenancy for a VDC that is created in an NSX Tenancy enabled Organization is “ON”. When the Networking Tenancy is enabled for a particular VDC, the Network Pool selection is disabled. That is because NSX supports Project creation only in the default overlay Transport Zone.

The Network Pool with the default overlay Transport Zone for the backing network provider has to exit beforehand. Otherwise, VCD will throw an error when creating Networking Tenancy enabled VDC.
Not all VDCs in a Project-aware organization need to participate in the Project. Suppose a different Geneve-backed Network Pool (non-default Transport Zone) or only VLAN networks are required in a VDC. In that case, the Provider can disable the Networking Tenancy and select the respective Network Pool.
However, it is essential to note that the Networking Tenancy (NSX Project participation) can only be specified during VDC creation. It cannot be changed afterward. Likewise, once a Provider enables the Networking Tenancy on VDC creation, they can not swap Network Pools.
VCD Model to NSX Projects
VCD makes the NSX Project management functions, such as creation, Tier-0 Gateway, and NSX Edge Cluster assignments, entirely transparent for both the Provider and the Tenant. When an Edge Gateway is created in a Networking Tenancy enabled VDC, VMware Cloud Director takes care of the respective NSX Edge Cluster and Tier-0 Gateway to be shared with the Project.
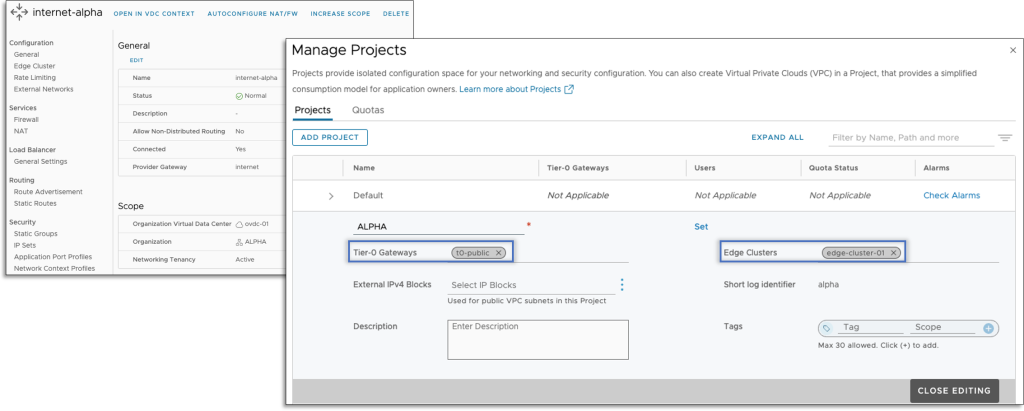
NSX segments associated with external and imported networks do not need to be part of the Project. If necessary, VCD takes care of these external components to be associated with Project components via an NSX Resource Share. When the connection is removed, the share is updated accordingly.
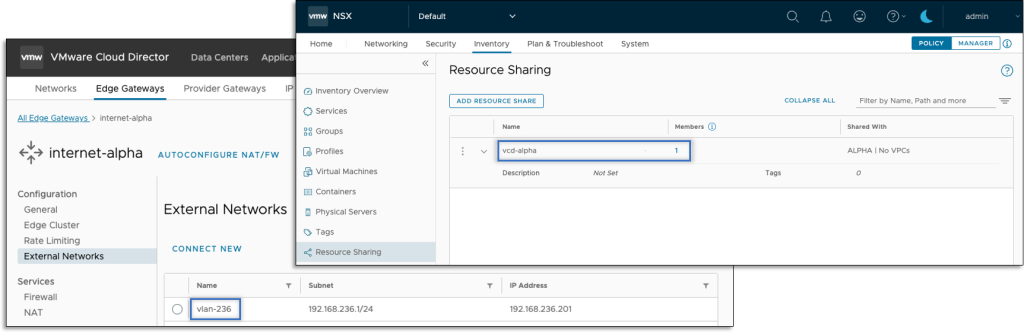
Data Center Groups support
The NSX Project is exclusively owned by the Organization that created it. The DC Group starting VDC type (Networking Tenancy enabled or not) determines whether the DC Group will have the Networking Tenancy active. It’s not mandatory for all VDC members of the DC Group to have an active Networking Tenancy. VMware Cloud Director supports a mixed mode where a DC Group has both Networking Tenancy active VDCs and Networking Tenancy inactive VDCs.
The NSX Project associated with the starting VDC is the one that will be used for all DC Group networking and security objects. Edge Gateways, Networks, Distributed Firewall Rules, Security Groups, etc., will sit within the scope of that NSX Project.
Unsupported features
Currently, NSX Projects is not a supported feature for NSX Federation deployments. Also, not all Edge Gateway features are available for Networking Tenancy enabled VDCs or DC Groups. VPNs (IPsec/L2) and sharing segment profile templates are the main notables.
To lear more about the NSX Projects supportability matrix: Features Available for Consumption Under NSX Projects
In Conclusion
By matching the NSX Projects with VCD’s Tenancy, customers will benefit from a wide range of networking capabilities the NSX Multi-tenancy solution provides. One of these critical features is tenant-focused logging for core VCD networking services such as Edge Services and Distributed firewalls.
Currently, the main platform for providing log access within VCD is VMware Aria Operations (a.k.a. LogInsight). Aria Operations is part of the base VMware Cloud Provider Platform (VCPP) bundle and, therefore, is available for all providers at no charge as part of the VCPP program.
NSX Projects logs from the Distributed and Gateway firewalls are labeled with the NSX Project log identifier, providing easy identification and separation per Tenant.
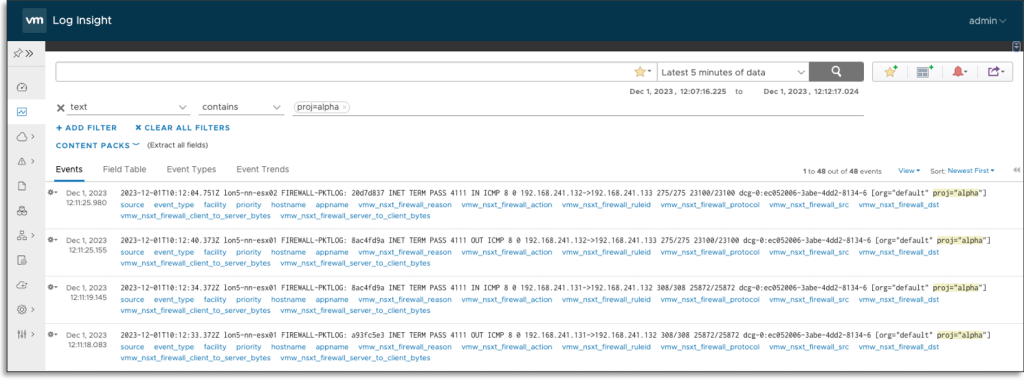
The integration with NSX Projects will also allow exploring the possibility of feature improvements to provide tenant self-service login capabilities in VCD.
Below, you can find more information about VMware Cloud Director 10.5.1’s new features and capabilities.
Remain up-to-date by regularly checking this blog for the latest updates. You can also connect with us on Slack, Facebook, Twitter, and LinkedIn.
Stay tuned for new demo videos and enablement on YouTube, especially our Feature Fridays series.
