In a recent analysis by HP, there’s a worrying trend in the world of cybercrime: easily accessible, pre-packaged malware kits are on the rise, allowing even those with limited tech know-how to launch sophisticated attacks.
Here’s what you should know:
- Old Malware in New Packaging: A strategy has emerged where attackers are hiding old malware, like the decade-old Houdini VBScript RAT, inside seemingly innocuous files, such as shipping documents. It’s a stark reminder that even old threats can return in new guises.
- Deceptive Double-Dealing Attacks: Some attackers are using a tactic where two actions kick off from a single malicious document. One displays a legitimate-looking invoice, distracting the user, while the other quietly runs harmful malware in the background. Notably, the tools for such attacks are available for as low as $65 a month on hacking forums.
Alex Holland from HP, a senior malware analyst, remarked on the ease with which these attacks can be executed. “With the rise of ‘DIY malware kits’, attackers don’t need to be tech wizards. They just buy these kits, which can exploit legit tools, making detection even harder.”
Interestingly, the report also highlighted a sneaky trick where some cybercriminals are misleading newbies. Fake malware-building kits are being sold on platforms like GitHub, tricking inexperienced hackers into accidentally infecting their own devices.
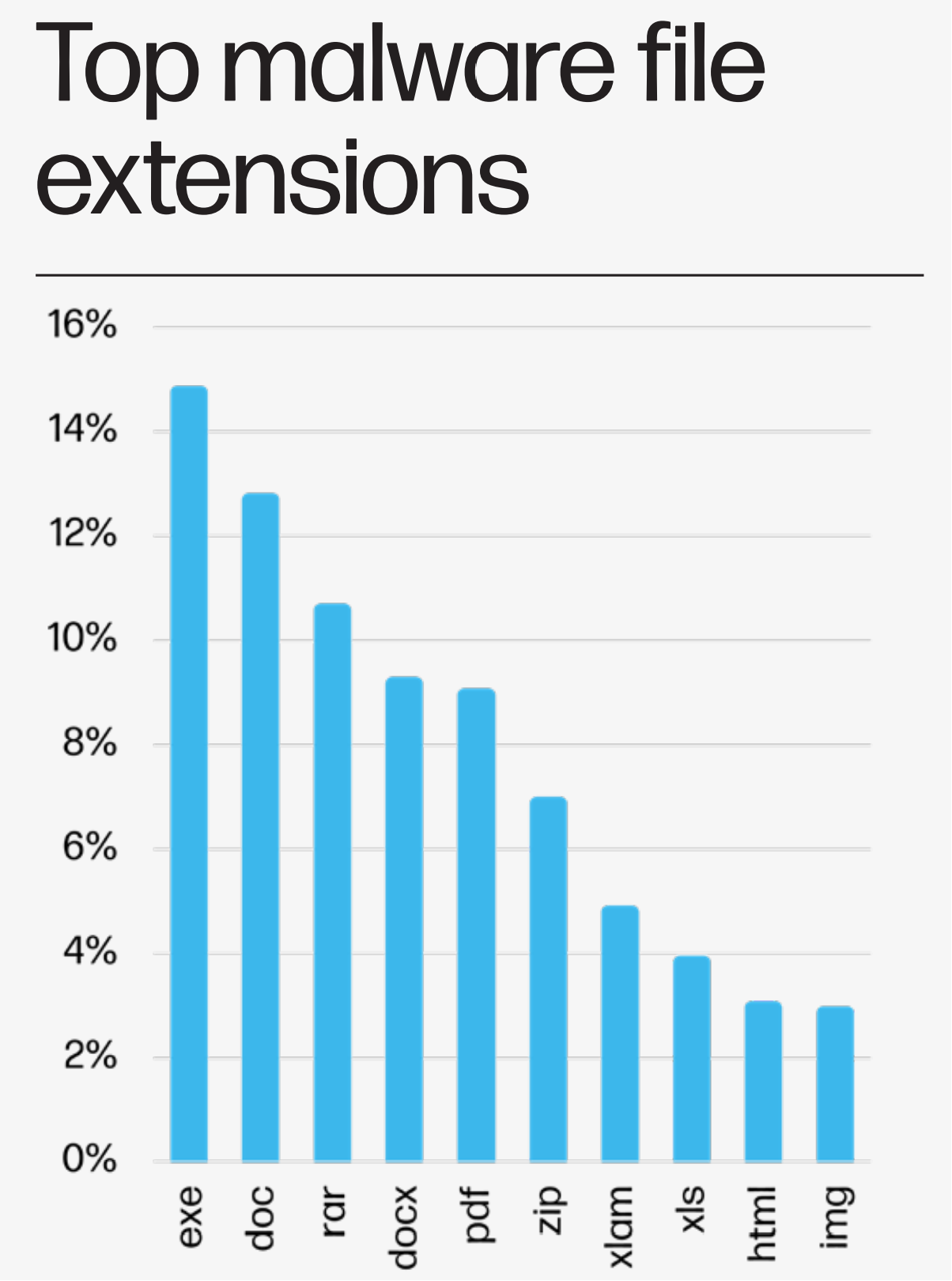
Top Malware File Extensions
The HP Wolf Security Threat Insights Report for Q3 2023 emphasizes the diverse range of file extensions being exploited by malware developers. Most notably, executable files (.exe) remain a primary choice for malware distribution. Traditional document formats like .doc, .docx, and .pdf continue to be exploited, underscoring the importance of treating even familiar file types with caution. The prominence of compressed formats like .rar and .zip highlights the need for rigorous security protocols when unpacking archives. As cyber threats evolve, understanding and awareness of such malware vectors remain crucial for proactive defense.

Some other important findings from HP’s analysis:
- Archives as Malware Carriers: For the sixth time in a row, archives remain the favorite method for malware delivery.
- Rise in File Extension Misuse: There’s been an alarming rise in the misuse of macro-enabled Excel add-ins and PowerPoint add-ins for malware distribution.
- Uncaught Threats: A surprising 12% of email threats slip through email gateway scanners, as identified by HP’s Sure Click tool.
- Increased Exploits in Common Tools: Q3 saw a significant rise in malware exploiting both Excel (91%) and Word (68%).
- PDFs as Threats: Malware contained in PDFs increased by 5% in Q3.
- Primary Attack Sources: Most cyberattacks in Q3 came via email (80%), with browser downloads being the second most common source (11%).
Holland suggests a defensive strategy: “Given how accessible these malware kits have become, businesses should focus on isolating tasks that are more vulnerable, like viewing email attachments or clicking on links. It’s all about reducing the opportunities for malware to get in.”
In essence, HP’s analysis underscores the need for constant vigilance and adaptation in cybersecurity strategies. With tools like HP’s Wolf Security, risky tasks are isolated in virtual environments, helping to minimize threats and providing insights into evolving cybercrime tactics.
By Randy Ferguson