Why you can trust us
- 407 Cloud Software Products and Services Tested
- 3056 Annual Software Speed Tests
- 2400 plus Hours Usability Testing
Our team of experts thoroughly test each service, evaluating it for features, usability, security, value for money and more. Learn more about how we conduct our testing.
Key Takeaways: What’s the Difference Between the Deep Web and the Dark Web?
- The deep web is used for hosting paywalled and password-protected websites, whereas the dark web is used for hosting encrypted websites, primarily for illegal activity.
- The deep web’s primary purpose is to restrict access to information and data, whereas the dark web’s primary purpose is to offer anonymity.
- Deep websites are accessible via regular web browsers, whereas dark websites can only be accessed through anonymizing browsers like Tor.
Facts & Expert Analysis:
- Accessing the Deep Web: The Deep Web makes up the majority of content on the internet and many people use pages on the deep web every day for things like work, school and online banking, among other use-cases.
- Finding the Dark Web: Dark Web traffic uses a special type of protocol known as TOR, meaning you need a compatible browser or browser extension to access those websites.
Best VPN for the Deep & Dark Webs
The terms “dark web” and “deep web” are often conflated and used interchangeably, mainly because the former is part of the latter. As you’ll learn in our comprehensive dark web vs deep web guide, the deep web encompasses websites that are hidden via non-indexing, paywalling and password protection, whereas the dark web only comprises non-indexed websites.
However, that’s just one of the main differences between the two — we’ll discuss more in this guide. We’ll dissect the dark web and the deep web to reveal how they work and their underlying technologies. We’ll also highlight the risks and show you how to access each section of the internet without jeopardizing your digital security or privacy.
Meet the experts
Learn more about our editorial team and our research process.
What Is the Deep Web?
The deep web resides just beneath the surface web, and it comprises content and services largely inaccessible to regular internet users. Though some content and services on the deep web are obscured through non-indexing, the majority are hidden through paywalling and password protection. Most of the deep web’s content and services are accessible via regular web browsers.
Examples of content and services on the deep web include:
- Internet banking
- Pay-to-access services like Netflix
- Email and social media accounts
- Private databases
- Data broker repositories and other privately protected file collections
- Academic content stored in university databases
- Government websites and company intranets
- HIPAA-sensitive information like electronic health records
Use Case Examples
Some popular use cases for the deep web include:
- Protecting user data and privacy: Educational institutions, governments and corporations host internal networks (intranets) and databases on the deep web to protect personal information and user privacy.
- Generating money via subscribership: Pay-to-access services hide content behind paywalls to compel users to pay to access on-demand, Software-as-a-Service (SaaS) and other technology services. Users without online accounts and those who haven’t paid for a subscription are locked out.
- Preventing unauthorized access: Financial institutions and other free-to-use services like social media and messaging app providers use the deep web to ensure that only users with the proper credentials can access accounts.
- Running digital marketing campaigns: Digital marketers may have a web page hidden on the deep web for a section of their target audience to track campaigns.
What Is the Dark Web?
The dark web is the smallest and least accessible subsection of the hidden web. It contains purely non-indexed websites and services. Dark web content and services are deliberately buried under layers of technology for anonymity and are only accessible through anonymizing web browsers like The Onion Router (Tor).
The anonymity and privacy the dark web offers make it a popular springboard for crime. As a result, it’s replete with illegal and illicit activity, such as drug dealing and arms trafficking. The dark web marketplace is also fraught with malware, Malware-as-a-Service (MaaS) and stolen data (such as online credentials and credit card numbers) for sale.
Use Case Examples
Beyond nefarious activity, the dark web has some good use cases, including:
- Sharing information anonymously: Journalists, whistleblowers, human rights defenders and political activists in autocratic nations use the dark web to share sensitive information without fear of eavesdropping. Law enforcement agencies have also established platforms on the dark web to enable users to share information without fear of retribution.
- Promoting free speech: The dark web is a lifeline for internet users such as protesters in oppressive regimes like China and North Korea. It provides the safety they need to speak freely without fear of prosecution.
- Bypassing censorship and surveillance: The dark web enables residents of restrictive regimes to access content and information unavailable on the open web.
The Main Differences Between the Dark Web & the Deep Web
The difference between the dark web and the deep web is that the former is a subsection of the deep web that’s better guarded and harder to reach. However, there are other subtle differences regarding their technologies, applications, scope and size, access and legality. Let’s get into the details:
1. Dark Web vs Deep Web: Technologies
Though the dark web is a subsection of the deep web, their underlying technologies differ.
The deep web doesn’t use unique methods to hide or serve content — it uses the same technologies the surface web relies on. The only difference is that many deep websites are either paywalled or password-protected. Some educational facilities and government websites use firewalls and intranets to restrict access to content.
On the other hand, the dark web uses darknets like Tor, Freenet, Riffle or other anonymized and encrypted networks as the underlying technology. These networks live on the fringes of the hidden web, offering many layers of encryption to protect data in transit. This encryption provides privacy and anonymity on the dark web.
2. Scope and Size
The deep web makes up approximately 95% of the internet. Beyond the paywalled and pay-to-access content, the deep web has crawlable web pages that aren’t indexed because the owners have blocked search engine crawlers from accessing them. This includes websites in the design stage and draft blogs in content management systems such as WordPress.
The dark web has a narrower scope, comprising a collection of purely non-indexed websites not searchable via regular web browsers. Most dark websites are used for illegal and illicit activity, but a few legal sites exist. According to Brittanica, the dark web makes up 0.01% of the deep web.
3. Applications
The main application of the deep web is to restrict access to information and data. For example, hospitals hide medical records to protect user privacy, while financial institutions use password protection to prevent unauthorized access. Educational institutions and government institutions use firewalls and intranets to keep the public and unauthorized users at bay.
The deep web also facilitates the sale of digital services and content, such as SaaS tools and on-demand content.
On the other hand, the dark web’s main application is to provide anonymity to website owners and users. The obscurity makes the dark web the perfect platform to host websites for illegal and illicit activity.
However, anonymity on the dark web isn’t used exclusively for insidious activity. It also gives political dissidents, journalists and whistleblowers the protection they need to share sensitive information.
4. Access and User Experience
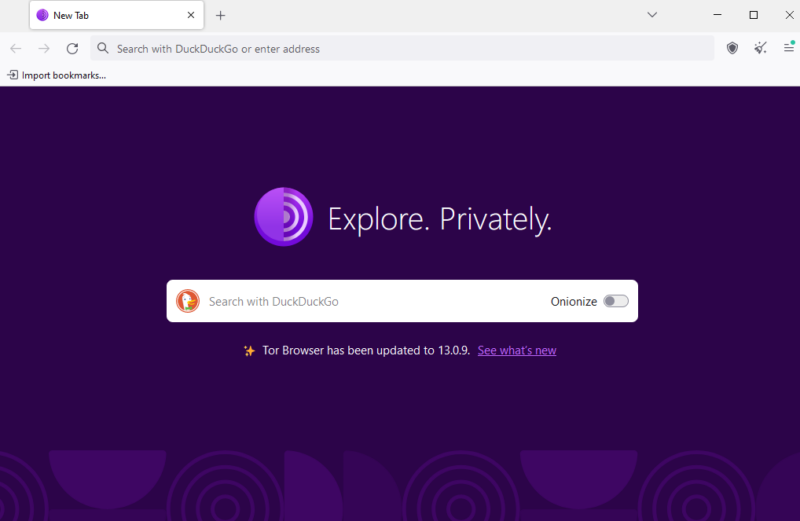
Tor is the best onion browser for accessing websites not indexed by regular web crawlers.
Deep Web sites and services are easily accessible via web browsers like Google Chrome, Firefox and Microsoft Edge. The difference from surface websites is that most deep websites require users to pay for a subscription or create an online profile to obtain login credentials.
The internet experience on the deep web is devoid of hurdles. Since you use regular web browsers and search engines, the search experience is seamless.
Dark Web sites and services are only accessible through purpose-built software, mainly anonymizing browsers. Tor is the go-to dark web browser, but other viable options like Brave, Epic and SRWare Iron exist.
The Tor browser uses the DuckDuckGo search engine, which makes anonymous internet browsing on the dark web flawless. Beyond DuckDuckGo, other options like AHMIA and Torch offer a dark web browsing experience reminiscent of browsing the web in the late 1990s.
5. Legality of the Dark Web and the Deep Web
Significant portions of the deep web are perfectly legal and safe to use. After all, there’s nothing illegal about accessing your email, social media, university website, banking website or other online services. However, illegally accessing deep web content and services, such as hacking into an account, is a criminal offense.
Accessing the dark web is legal, but what you do on the dark streets matters. If you engage in any criminal activity and you’re caught in the act, you could face the full force of the law.
Deep Web vs Dark Web: Risks
Visiting the dark or deep web for legitimate purposes doesn’t mean you’re entirely safe. Just like the surface web, the two sections are constantly grappling with risks of their own. Let’s explain:
Deep Web Risks
Though deep web content and services are largely safe and legal, the risk of your login credentials falling into the wrong hands is real. Remember that nearly all the websites you access on the deep web require password authentication.
Most websites, like internet banking, government institutions, social media platforms and healthcare institutions, hold valuable personal data — a treasure trove for cybercriminals.
Login credentials are gateways to this data, which is why they attract the attention of hackers and other malicious actors. Watch out for fake login prompts, phishing emails and other hacking methods that hackers cook up to steal your passwords and gain access to your accounts.
Dark Web Risks
Dark web risks emanate from the vulnerabilities of its underlying technology — the Tor network. Global volunteers run the servers in the Tor chain. You cannot predict each Tor operator’s intention. If malicious actors operate an exit node, they can infect your traffic or downloads with worms, trojans or keyloggers.
Another factor to note is that while your traffic is encrypted several times, it’s not encrypted as it exits the last server in the chain. Law enforcement officials in some countries have been found to run or seize exit nodes to monitor dark web traffic. If your traffic passes through a compromised node, the authorities can see your real IP address and potentially trace the activity back to you.
Deep Web Safety Tips
Cybercriminals roam the deep web looking to steal credentials and gain entry into your online accounts. To thwart these deep web risks, follow these guidelines:
- Create strong, unique login credentials: When creating accounts online, always set unique passwords that are difficult for hackers to decipher. You can use a password manager to ensure each account has a strong, unique password.
- Configure firewalls: For companies and organizations dealing with sensitive data, it’s good to configure firewalls that combine vital security functions. Besides encrypting data sent over the company network, next-generation firewalls offer solid virus and malware protection.
- Maintain sound cybersecurity procedures: Create solid cybersecurity policies outlining access to your databases and company intranets. Sensitize and educate employees on the importance of complying with cybersecurity policies.
Dark Web Safety Tips
To access the dark web safely, adhere to the following best practices:
- Download Tor from the official website: Tor is the dark web browser of choice for many users, and cybercriminals are aware of this. They set up traps to make unsuspecting users download a compromised version to infect their devices with viruses or malware. Download the Tor browser from the official Tor project website.
- Use a secure VPN: A virtual private network (VPN) with an anonymizing browser eliminates the risks associated with a compromised Tor exit server. The best VPN for the dark web encrypts traffic before it enters the Tor network. If a law enforcement agency intercepts the traffic, they can’t see your real IP address or trace the activity back to you.
- Practice online security precautions: Don’t open every onion URL you come across or you’ll end up landing on an illegal site. Before clicking, verify each URL’s authenticity on subreddits such as /r/Tor, /r/onions or /r/deepweb.
Best VPN for the Dark Web: ExpressVPN

ExpressVPN offers an extra layer of protection, making it difficult for hackers, internet service providers or government agencies to monitor your dark web activity.
ExpressVPN is the best VPN for the dark web by merit. Its secure protocols and encryption ensure that even if your traffic passes through a compromised node, the authorities can’t trace any activity back to you. It also has a kill switch, which cuts your internet connection to prevent IP leaks if the VPN disconnects.
In addition, ExpressVPN servers wipe data on every reboot thanks to TrustedServer technology. If a law enforcement agency seizes or infiltrates a server to investigate a user’s dark web activity, they will find no data or Tor browsing history. Learn more in our comprehensive ExpressVPN review.
ExpressVPN Plans
Final Thoughts
By now, you know what the deep and the dark web have in common and what sets them apart. Understanding how these parts of the internet work helps you protect your security and privacy as you navigate them.
We recommend using a VPN when visiting the deep and the dark web to add an extra layer of protection. ExpressVPN is the best VPN for the dark and the deep web thanks to its top-notch online privacy and security. Make the most of ExpressVPN’s 30-day money-back guarantee for risk-free deep or dark web exploration.
Have you visited the dark web or the deep web before? Which VPN or purpose-built software did you use to visit websites on the deep or the dark web? Did the dark web VPN and software meet your expectations? We’d like to hear about it in the comment section. As always, thanks for reading.
FAQ: Deep Web vs Dark Web
-
Yes, the deep web hosts paywalled and password-protected websites, whereas the dark web comprises purely non-indexed, encrypted websites.
-
Much illegal activity takes place on the dark web because this invisible internet project offers a high level of anonymity. However, beyond illegal activity, journalists, whistleblowers and political activists use the dark web as a safe platform to share information anonymously.
-
No, both the deep web and the dark web are perfectly legal, but using them for illegal activity is not.
Yes, the deep web hosts paywalled and password-protected websites, whereas the dark web comprises purely non-indexed, encrypted websites.n”}},{“@type”:”Question”,”name”:”What Happens on the Dark Web?”,”acceptedAnswer”:{“@type”:”Answer”,”text”:”
Much illegal activity takes place on the dark web because this invisible internet project offers a high level of anonymity. However, beyond illegal activity, journalists, whistleblowers and political activists use the dark web as a safe platform to share information anonymously.n”}},{“@type”:”Question”,”name”:”Are the Deep Web and the Dark Web Illegal? “,”acceptedAnswer”:{“@type”:”Answer”,”text”:”
No, both the deep web and the dark web are perfectly legal, but using them for illegal activity is not.n”}}]}]]>
Let us know if you liked the post. That’s the only way we can improve.

